Unlocking The Potential Of RemoteIoT Platform SSH Key
Hey there tech enthusiasts! If you're diving into the world of IoT (Internet of Things) and remote management, then you've probably come across the term "RemoteIoT platform SSH key." But hold your horses—what exactly does this mean, and why should you care? Well, buckle up because we're about to break it down in a way that even your grandma could understand. Think of an SSH key as a digital keycard that lets you access your IoT devices from anywhere in the world, without needing to remember a bunch of passwords. Sounds pretty cool, right? Let's dig in!
In today's fast-paced digital era, managing IoT devices remotely has become a necessity rather than a luxury. The RemoteIoT platform SSH key is like your backstage pass to the world of secure, seamless device management. It's not just about convenience; it's about safeguarding your data and ensuring your devices are as secure as Fort Knox. Whether you're a tech-savvy professional or a newbie, understanding this concept can revolutionize how you interact with your smart devices.
So, why are we so excited about this? Because the RemoteIoT platform SSH key isn't just another tech buzzword—it's a game-changer. It simplifies the process of managing IoT devices while keeping your data protected from prying eyes. In this article, we'll dive deep into what makes this technology so powerful, how it works, and why it's essential for anyone venturing into the IoT space. Ready to unlock the secrets? Let's go!
Read also:Lelasoha Erome The Rising Star In The Spotlight
What is RemoteIoT Platform?
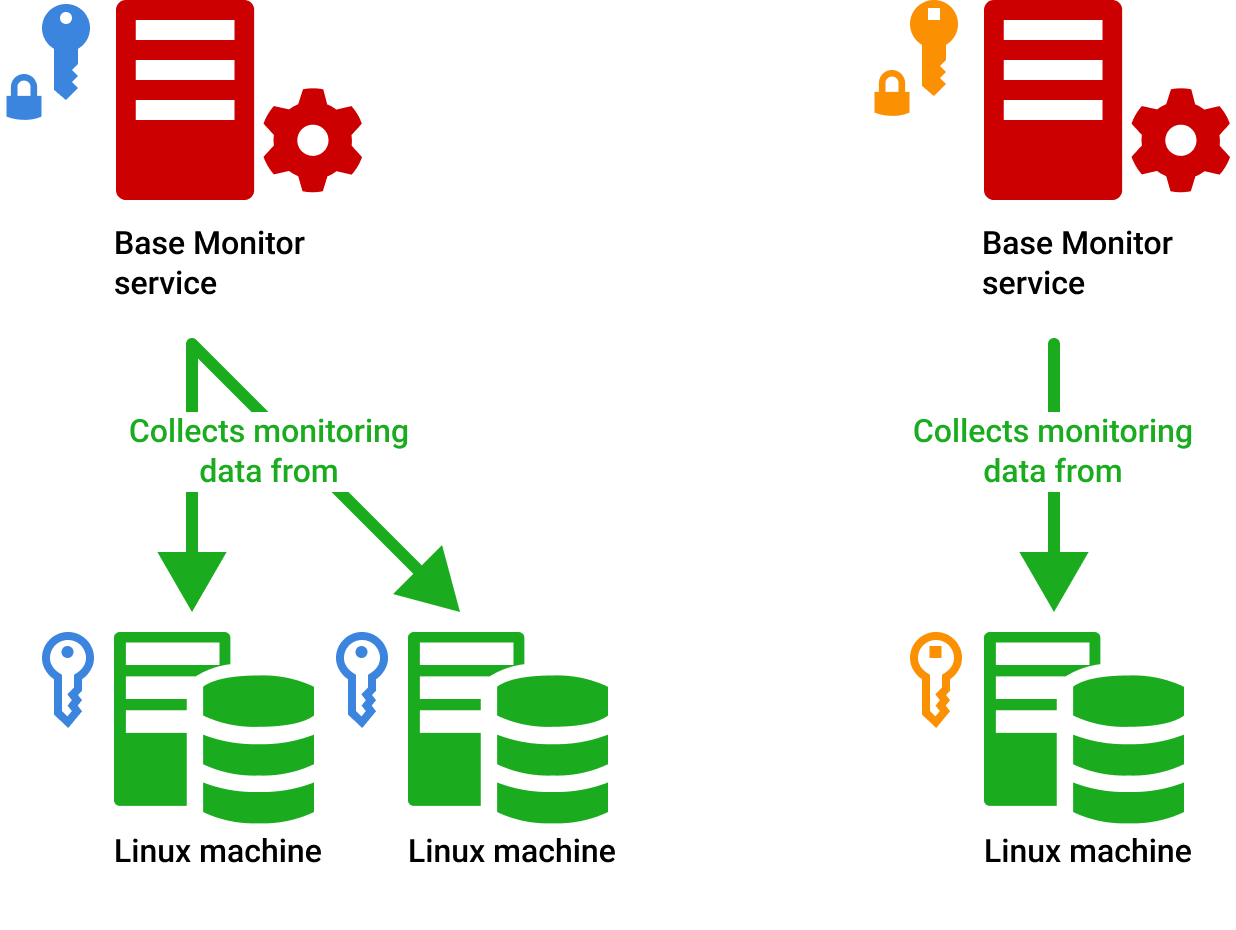
Alright, let's start with the basics. The RemoteIoT platform is essentially a system designed to help you manage and monitor IoT devices from afar. Imagine having a network of sensors, cameras, and other smart gadgets scattered across different locations. Without a centralized platform, managing all these devices can be a chaotic mess. That's where RemoteIoT comes in. It acts as the brain of your IoT ecosystem, allowing you to control everything from one place.
Now, here's the kicker: to make sure only authorized people can access your devices, the platform uses something called SSH keys. Think of these keys as digital bouncers at a club—they verify who's allowed in and who isn't. By using SSH keys, the RemoteIoT platform ensures that even if someone tries to hack into your system, they won't get far without the right credentials.
Understanding SSH Keys
So, what exactly are SSH keys? Simply put, they're pairs of cryptographic keys used for secure communication between devices. There's a public key, which is like your house address that you can share with others, and a private key, which is like the actual key to your front door—you keep that one super safe. When you use an SSH key to log into a device, the public key is stored on the device, and the private key stays with you. This way, only someone with the matching private key can access the device.
Why Use SSH Keys Over Passwords?
Here's the deal: passwords are so 2000 and late. They're easy to guess, easy to crack, and let's be honest, most of us are terrible at creating strong ones. SSH keys, on the other hand, are virtually impossible to brute force. Plus, they eliminate the need to remember complex passwords for every device you manage. It's like having a universal key that works everywhere, without the risk of losing it.
How RemoteIoT Platform SSH Key Works
Now that we know what SSH keys are, let's see how they integrate with the RemoteIoT platform. When you set up your IoT devices, you generate an SSH key pair. The public key is then uploaded to the RemoteIoT platform, while the private key remains securely on your device. Whenever you need to access a device, the platform uses the public key to verify your identity, and if everything checks out, you're granted access.
It's like a high-tech handshake. The platform says, "Hey, prove you're who you say you are," and your device responds with, "Here's my private key, and it matches your public key." Once the handshake is complete, you're good to go. No passwords, no hassle, just smooth, secure access to your devices.
Read also:What Do Crown Family Members Do For Society Unveiling Their Contributions
Benefits of Using RemoteIoT Platform SSH Key
Let's talk about the perks of using SSH keys with the RemoteIoT platform. First off, there's the obvious security advantage. With SSH keys, you don't have to worry about someone guessing your password or using a brute force attack to gain access. The level of encryption used in SSH keys makes them incredibly secure.
Then there's convenience. Imagine managing hundreds of IoT devices without having to remember a single password. Sounds like a dream, right? With SSH keys, you can log in to any device with just a few clicks. Plus, the RemoteIoT platform automates a lot of the process, so you don't have to be a tech wizard to use it effectively.
Increased Productivity
By streamlining the login process, SSH keys help you focus on what really matters—managing your IoT devices efficiently. Whether you're monitoring environmental sensors in a remote location or controlling smart home devices, having seamless access can boost your productivity significantly. You spend less time troubleshooting login issues and more time getting things done.
Setting Up SSH Keys on RemoteIoT Platform
Alright, let's get practical. How do you actually set up SSH keys on the RemoteIoT platform? Don't worry; it's not as complicated as it sounds. First, you'll need to generate an SSH key pair. Most operating systems come with tools to do this, like ssh-keygen on Linux and macOS. Once you've generated your keys, you'll need to upload the public key to the RemoteIoT platform.
Here's a quick rundown of the steps:
- Generate an SSH key pair using a tool like ssh-keygen.
- Copy the public key to your clipboard.
- Log in to the RemoteIoT platform and navigate to the SSH key settings.
- Paste the public key into the designated field and save it.
- That's it! You're now ready to securely access your devices.
Troubleshooting Common Issues
Sometimes, things don't go as planned. If you're having trouble setting up your SSH keys, here are a few tips:
- Make sure your public key is correctly formatted. It should start with "ssh-rsa" or a similar identifier.
- Check that your private key is securely stored and accessible only to you.
- Verify that the RemoteIoT platform is configured to accept SSH key authentication.
- If all else fails, consult the platform's documentation or reach out to their support team.
Security Best Practices
While SSH keys are incredibly secure, there are still some best practices you should follow to keep your devices safe:
- Never share your private key with anyone. Treat it like your most valuable secret.
- Store your private key in a secure location, preferably encrypted.
- Regularly update your SSH keys to prevent unauthorized access.
- Monitor access logs to detect any suspicious activity.
By following these practices, you can ensure that your RemoteIoT platform remains as secure as possible.
Real-World Applications
Now that we've covered the technical aspects, let's talk about how the RemoteIoT platform SSH key is used in real-world scenarios. From industrial automation to smart home management, the possibilities are endless. Companies use this technology to monitor and control equipment in remote locations, while individuals use it to manage their smart home devices from anywhere in the world.
For example, imagine a farmer using IoT sensors to monitor soil moisture levels in their fields. With the RemoteIoT platform and SSH keys, they can access this data from their smartphone, no matter where they are. It's like having a personal assistant for your IoT devices, always ready to provide the information you need.
Case Study: Smart City Implementation
In a smart city initiative, the RemoteIoT platform SSH key was used to manage a network of traffic sensors. By securely accessing these sensors from a central control room, city officials were able to optimize traffic flow and reduce congestion. This not only improved traffic conditions but also enhanced public safety and reduced pollution. It's a perfect example of how SSH keys can be used to create smarter, more efficient urban environments.
Future Trends in IoT Security
As the IoT space continues to evolve, so do the security measures surrounding it. Experts predict that SSH keys will become even more sophisticated, incorporating advanced encryption techniques and biometric authentication. This means that in the future, you might be able to log in to your devices using your fingerprint or face recognition, in addition to SSH keys.
Moreover, the integration of AI and machine learning into IoT security is on the rise. These technologies can help detect and respond to threats in real-time, making your devices even more secure. As we move forward, the RemoteIoT platform and SSH keys will undoubtedly play a crucial role in shaping the future of IoT security.
Conclusion
And there you have it—a comprehensive look at the RemoteIoT platform SSH key and why it's such a big deal. From enhancing security to boosting productivity, this technology offers a wide range of benefits for anyone managing IoT devices. By understanding how SSH keys work and following best practices, you can ensure that your devices remain secure and accessible from anywhere in the world.
So, what are you waiting for? Dive into the world of RemoteIoT and experience the power of SSH keys for yourself. And don't forget to share your thoughts and experiences in the comments below. Who knows? You might just inspire someone else to take the leap into the IoT revolution!
Table of Contents
- Unlocking the Potential of RemoteIoT Platform SSH Key
- What is RemoteIoT Platform?
- Understanding SSH Keys
- Why Use SSH Keys Over Passwords?
- How RemoteIoT Platform SSH Key Works
- Benefits of Using RemoteIoT Platform SSH Key
- Increased Productivity
- Setting Up SSH Keys on RemoteIoT Platform
- Troubleshooting Common Issues
- Security Best Practices
- Real-World Applications
- Case Study: Smart City Implementation
- Future Trends in IoT Security
- Conclusion